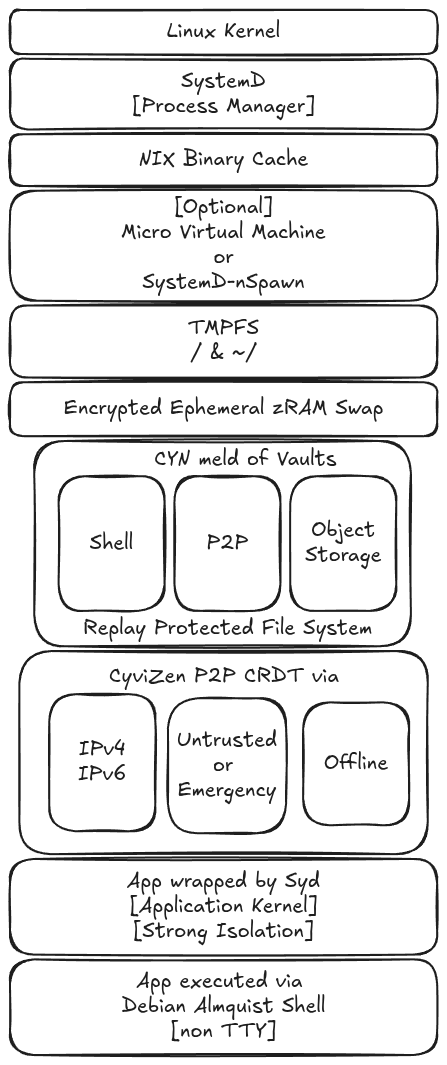
CyviZen: App Execution & Isolation
Application Security has become a frustratingly complex discussion.
At one end of the spectrum Qubes OS exists, in which Full Virtualisation is applied
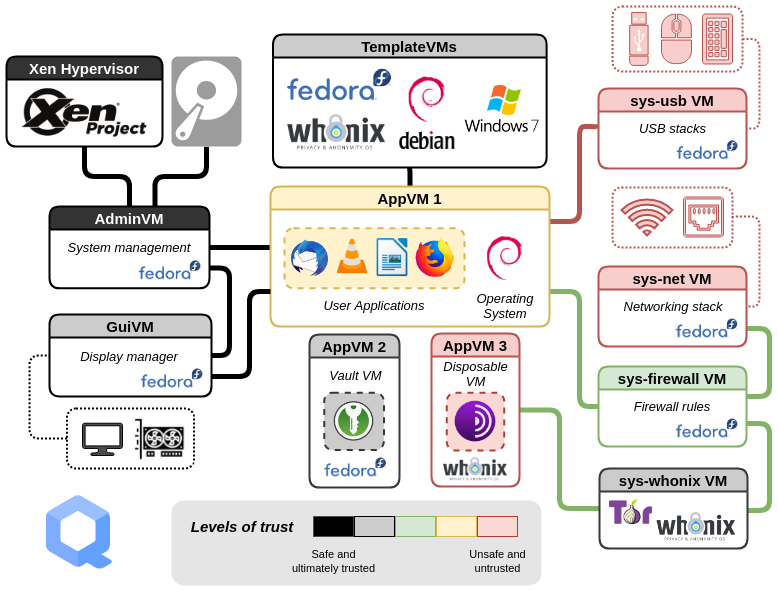
Qubes OS Architecture
At the other end of the spectrum, eBPF is available directly in the Linux Kernel to Sandbox Applications, however it requires privileged kernel context to be enabled
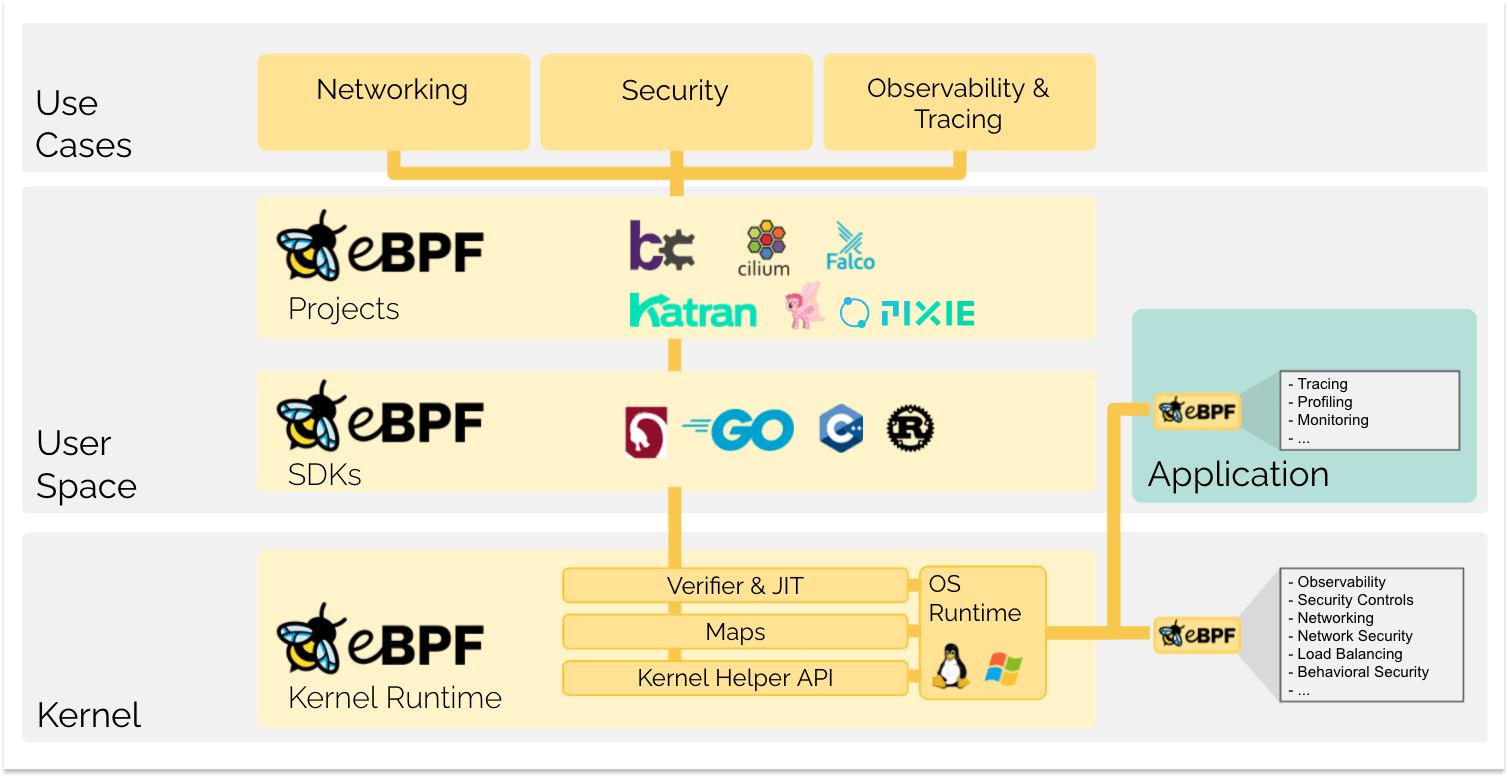
eBPF Architecture
CyviZens tagline Responsibility is Power, implies that the more you choose to be responsible the more CyviZen can grant you power. In terms of App Execution & Isolation this is 100% true, where the power granted by CyviZen to you far exceeds what is possible via Qubes OS or eBPF.
Excution pathway for all Apps within CyviZen is visible on the right:
- NIX ensures that all Apps build are globally reproducibly and idempotent
- Qubes style can be achived via Micro Virtual Machines, and nSpawnD Containers are used for privileged services
- CyviZen as an OS is Immutable & Ephemeral By Default
- CyviZen has per-folder vaults, every folder can be anywhere in the world overlayed on a replay attack resiliant filesystem
- Syd provides a Rock-Solid Application Kernel that implements a subset of the Linux kernel interface in user space, intercepting system calls to provide strong isolation without the overhead of full virtualization. Syd is secure by default, and intends to provide a simple interface over various intricate Linux sandboxing mechanisms such as LandLock, Namespaces, Ptrace, and Seccomp-{BPF,Notify}
Finally CyviZen executes Apps via Debian Almquist Shell (DASH) in a non-TTY environment